Balancer Hack Onchain Analysis Reveals Sophisticated Attack
Background on the $116 Million Balancer Hack
The decentralized exchange and automated market maker, Balancer, suffered a significant security breach on Monday as hackers exploited its smart contracts to drain approximately $116 million in digital assets. New Balancer hack onchain analysis indicates the attack was carried out by a highly skilled operator employing advanced tactics and long-term planning to avoid detection.
Onchain data demonstrated that the attacker incrementally funded their account using small 0.1 Ether (ETH) transactions originating from the cryptocurrency mixer Tornado Cash. Conor Grogan, director at Coinbase, highlighted that the exploiter maintained at least 100 ETH in Tornado Cash smart contracts. “Hacker seems experienced: 1. Seeded account via 100 ETH and 0.1 Tornado Cash deposits. No opsec leaks,” Grogan posted on X, suggesting that the individual may have been involved in previous cyber attacks.
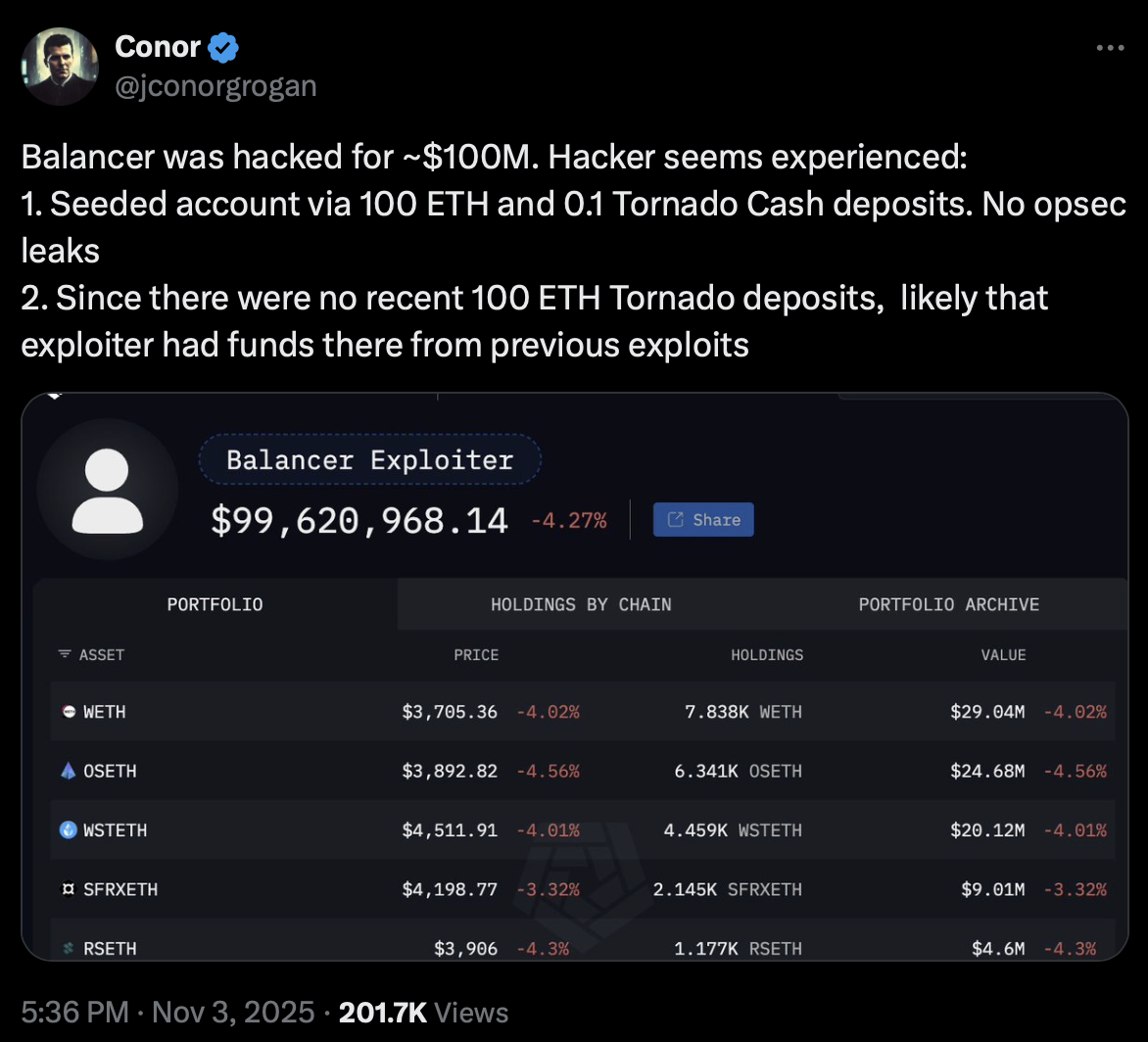
Few users typically keep large sums in privacy mixers, reinforcing suspicions about the attacker’s professionalism and prior experience. Reporting via Cointelegraph.
Attacker Methods and Response from Balancer
The Balancer hack onchain analysis suggests that the preparation for this attack may have spanned several months, with careful steps taken to avoid leaving traces. Security experts believe the absence of operational security (opsec) mistakes demonstrates the high level of expertise involved.
Following the exploit, Balancer extended a 20% white hat bounty to the perpetrator, offering to let them keep that portion if the stolen assets were returned by Wednesday. “Our team is working with leading security researchers to understand the issue and will share additional findings and a full post-mortem as soon as possible,” Balancer wrote in a recent X update.
Deddy Lavid, co-founder and CEO of blockchain security firm Cyvers, remarked that this incident ranks among “the most sophisticated attacks we’ve seen this year,” noting the need for constant and real-time threat monitoring on blockchain platforms rather than reliance on static code audits.
Comparisons to Recent Crypto Attacks and Market Reactions
Comparisons were drawn to past hacks orchestrated by the North Korean Lazarus Group, who are also known for methodical planning and the use of privacy tools. Eric Jardine, cybercrimes research lead at blockchain analytics firm Chainalysis, reported a noticeable decline in illicit North Korean-linked activities after July 1, 2024, stating: “The slowdown that we observed could have been a regrouping to select new targets, probe infrastructure, or it could have been linked to those geopolitical events,” he told Cointelegraph.
The Lazarus Group reportedly took 10 days to launder 100% of funds from the Bybit exchange hack, primarily using cross-chain protocols such as THORChain. This pattern underscores the sophistication and persistent threat from advanced hacking groups in the decentralized finance (DeFi) sector, as illustrated by the Balancer hack onchain analysis.
What’s Next for Balancer and DeFi Security?
In response to this exploit, Balancer is collaborating with security researchers and promised a public post-mortem of the incident. The recurring nature of such sophisticated attacks highlights growing challenges for DeFi platforms and underscores the need for adaptive, continuous monitoring systems. Security experts are advocating for the industry to move beyond traditional auditing and toward integrating dynamic, ongoing security solutions.
For more updates on major crypto security stories and DeFi technology, visit Vizi’s cryptocurrency section.



















